HTTP Proxies
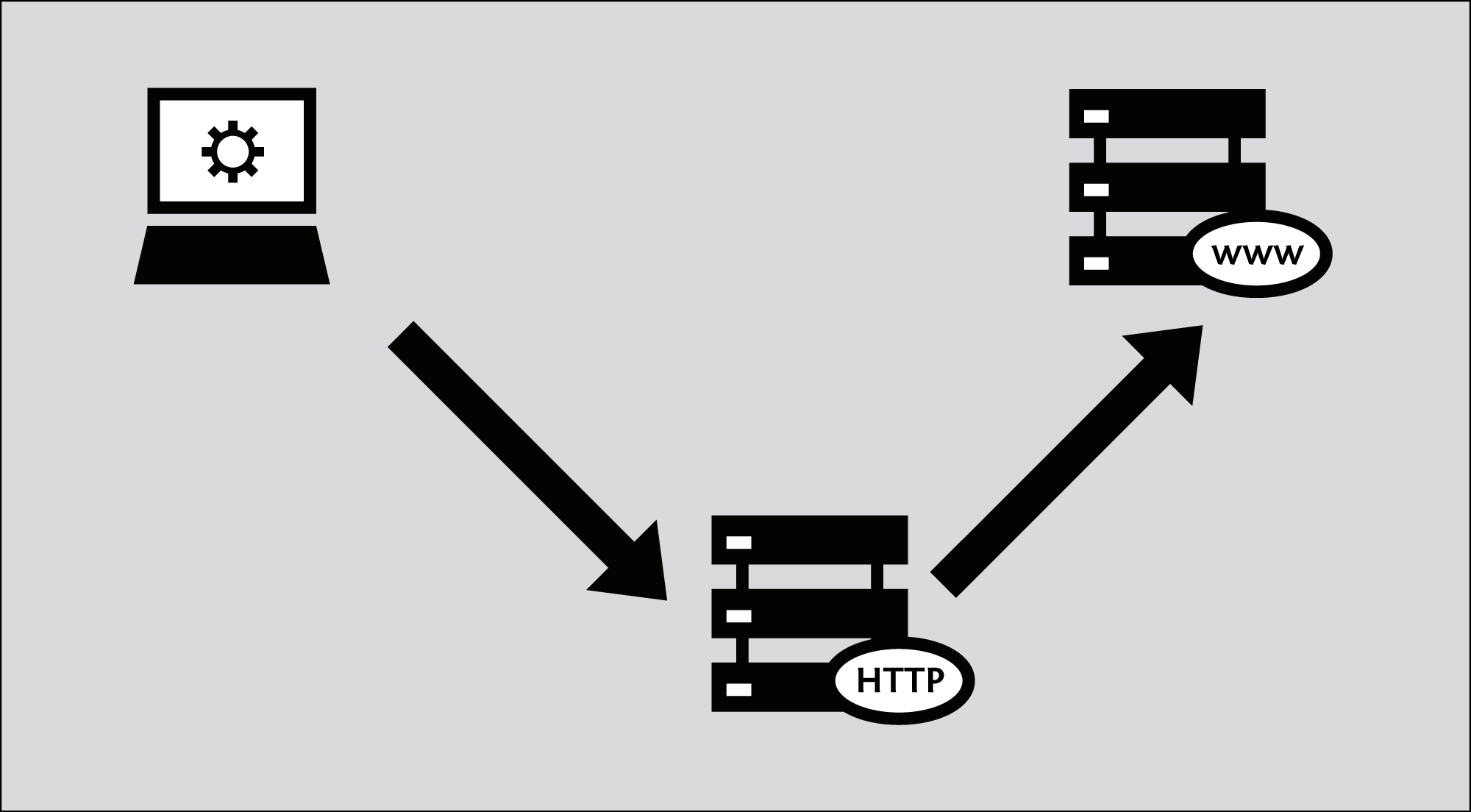
Software called an application proxy enables one computer on the Internet to process requests from another computer. The most common kinds of application proxies are HTTP proxies, which handle requests for Web sites, and SOCKS proxies, which handle connection requests from a wide variety of applications. In this chapter we will look at HTTP proxies and how they work.
Good proxies and bad proxies
Application proxies can be used by network operators to censor the Internet or to monitor and control what users do. However, application proxies are also a tool for users to get around censorship and other network restrictions.
Proxies that restrict access
A network operator may force users to access the Internet (or at least Web pages) only through a certain proxy. The network operator can program this proxy to keep records of what users access and also to deny access to certain sites or services (IP blocking or port blocking). In this case, the network operator may use a firewall to block connections that do not go through the restrictive proxy. This configuration is sometimes called a forced proxy, because users are required to use it.
Proxies for circumvention
However, an application proxy can also be helpful for circumventing restrictions. If you can communicate with a computer in an unrestricted location that is running an application proxy, you can benefit from its unrestricted connectivity. Sometimes a proxy is available for the public to use; in that case, it's called an open proxy. Many open proxies are blocked in Internet-restricting countries if the people administering the network restrictions know about them.
Where to find an application proxy
There are many Web sites with lists of open application proxies. An overview of such sites is available at http://www.dmoz.org/Computers/Internet/Proxying_and_Filtering
/Hosted_Proxy_Services/Free/Proxy_Lists.
Please note that many open application proxies only exist for a few hours, so it is important to get a proxy from a list which was very recently updated.
HTTP Proxy settings
To use an application proxy, you must configure the proxy settings for your operating system or within individual applications. Once you have selected a proxy in an application's proxy settings, the application tries to use that proxy for all of its Internet access.
Be sure you make note of the original settings so that you can restore them. If the proxy becomes unavailable or unreachable for some reason, the software that is set to use it generally stops working. In that case, you may need to reset to the original settings.
On Mac OS X and some Linux systems, these settings can be configured in the operating system, and will automatically be applied to applications such as the web browser or instant messaging applications. On Windows and some Linux systems, there is no central place to configure proxy settings, and each application must be configured locally. Bear in mind that, even if the proxy settings are configured centrally, there is no guarantee that applications will support these settings, so it is always a good idea to check the settings of each individual application.Typically only Web browsers can directly use an HTTP proxy.
The steps below describe how to configure Microsoft Internet Explorer, Mozilla Firefox, Google Chrome and the free and open source instant messaging client Pidgin to use a proxy. If you use Firefox for Web browsing, it may be simpler to use the FoxyProxy software; it is an alternative to the steps below. If you use Tor, it is safest to use the TorButton software (which is provided as part of the Tor Bundle download) to configure your browser to use Tor.
While e-mail clients such as Microsoft Outlook and Mozilla Thunderbird can also be configured to use HTTP proxies, actual e-mail traffic when sending and fetching e-mail uses other protocols such as POP3, IMAP and SMTP; this traffic will not pass through the HTTP proxy.
Mozilla Firefox
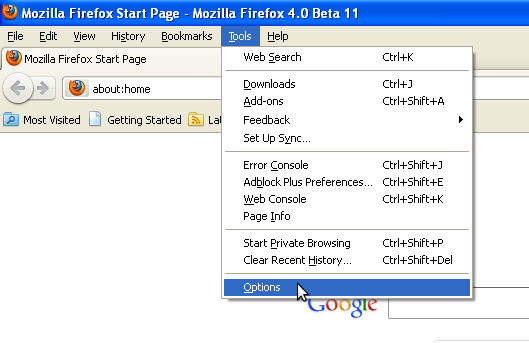
To configure Firefox to use an HTTP proxy:
- Select Tools > Options:
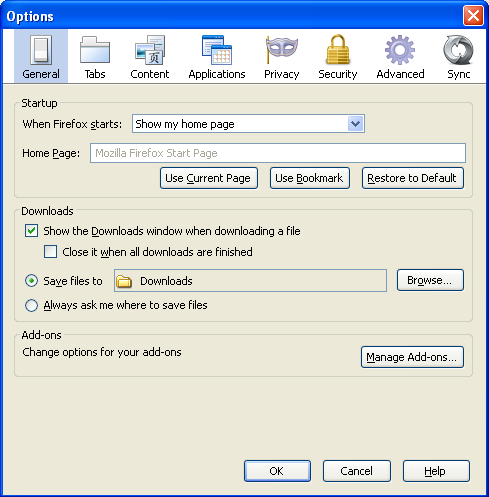
- The Options window appears:
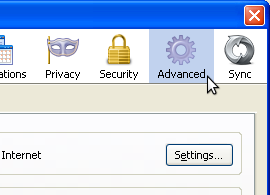
- In the toolbar at the top of the window, click Advanced:
- Click the Network tab:
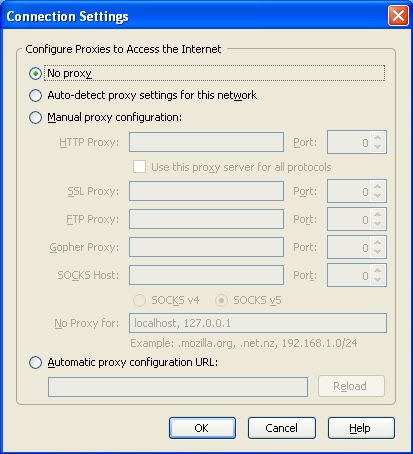
- Click Settings. Firefox displays the Connection Settings window:
- Select "Manual proxy configuration". The fields below that option become available.
- Enter the HTTP proxy address and port number, and then click OK.
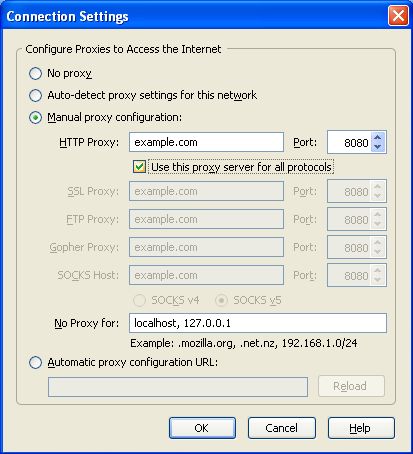
If you click "Use this proxy server for all protocols", Firefox will attempt to send HTTPS (secure HTTP) and FTP traffic through the proxy. This may not work if you are using a public application proxy, since many of these do not support HTTPS and FTP traffic. If, on the other hand your HTTPS and/or FTP traffic is being blocked, you can try to find a public application proxy with HTTPS and/or FTP support, and use the "Use this proxy server for all protocols" setting in Firefox.
Now Firefox is configured to use an HTTP proxy.
Microsoft Internet Explorer
To configure Internet Explorer to use an HTTP proxy:
- Select Tools > Internet Options:
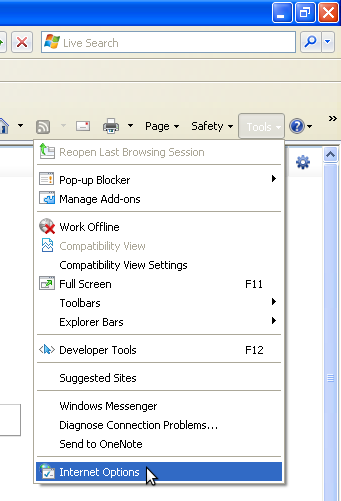
- Internet Explorer displays the Internet Options window:
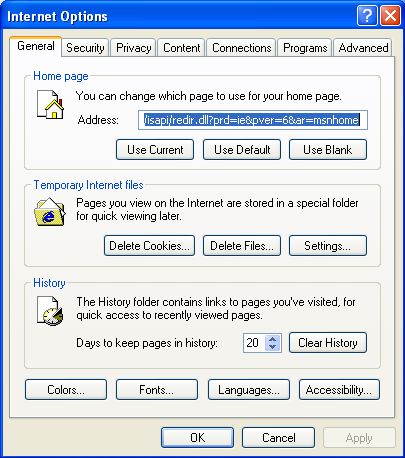
- Click the Connections tab.
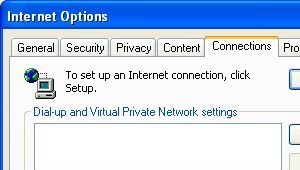
- Click LAN Settings. The Local Area Network (LAN) Settings window appears.
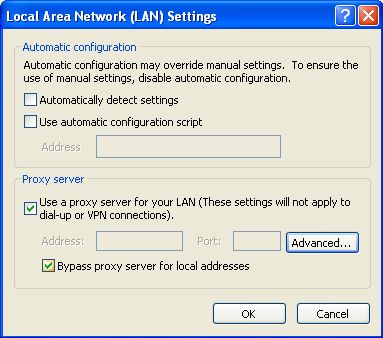
- Select "Use a proxy server for your LAN".
- Click Advanced. The Proxy Settings window appears.
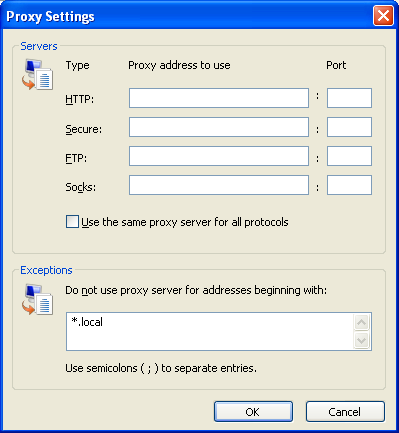
- Enter the proxy address and port number in the first row of fields.
- If you click "Use the same proxy server for all protocols", Internet Explorer will attempt to send HTTPS (secure HTTP) and FTP traffic through the proxy. This may not work if you are using a public application proxy, since many of these do not support HTTPS and FTP traffic. If, on the other hand your HTTPS and/or FTP traffic is being blocked, you can try to find a public application proxy with HTTPS and/or FTP support, and use the "Use this proxy server for all protocols" setting in Internet Explorer.
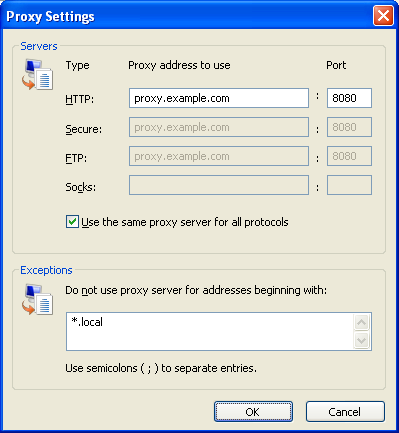
Now Internet Explorer is configured to use an HTTP proxy.
Google Chrome
Google Chrome uses the same connection and proxy settings as the Windows operating system. Changing these settings affects Google Chrome as well as Internet Explorer and other Windows programs. If you configured your HTTP proxy through Internet Explorer then you don't need to take this steps to configure Chrome.
Follow these steps to configure your HTTP proxy:
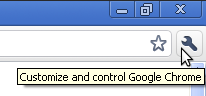
- Click on the "Customize and control Google Chrome" menu (the little wrench next to the URL address bar):
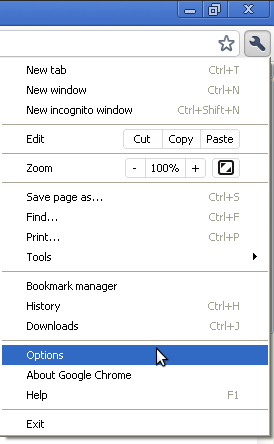
- Click on Options:
- In the Google Chrome Options window, select the Under the Hood tab:
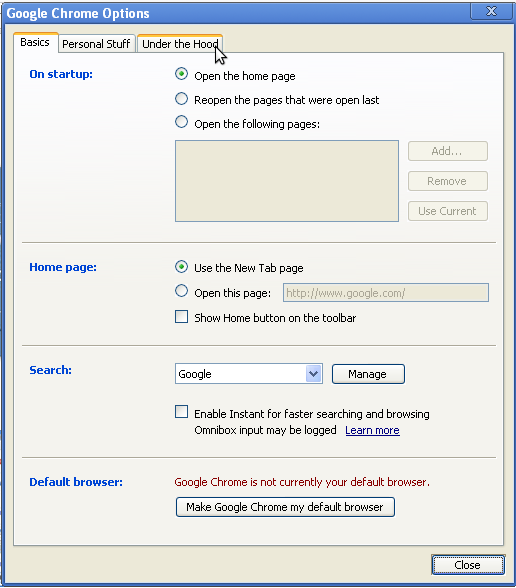
- In the Network section, click the "Change proxy settings" button:
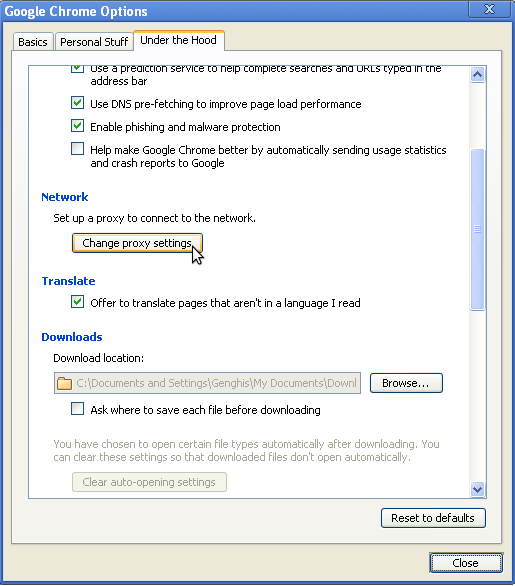
- The Internet Options window will open. Follow steps 2-8 from "How to configure the HTTP Proxy under Internet Explorer" (above) to finish setting up your HTTP proxy.

Chrome is now configured to use HTTP proxy.
Pidgin instant messaging client
Some Internet applications other than Web browsers can also use a HTTP proxy to connect to the Internet, potentially bypassing blocking. Here is an example with the instant messaging software Pidgin.
- Select Tools > Preferences:
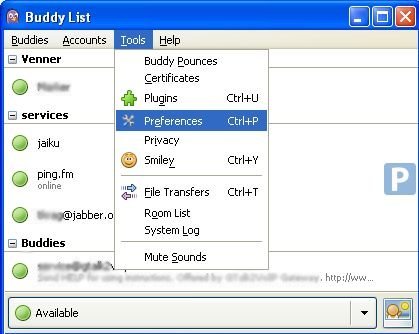
Pidgin displays the Preferences window: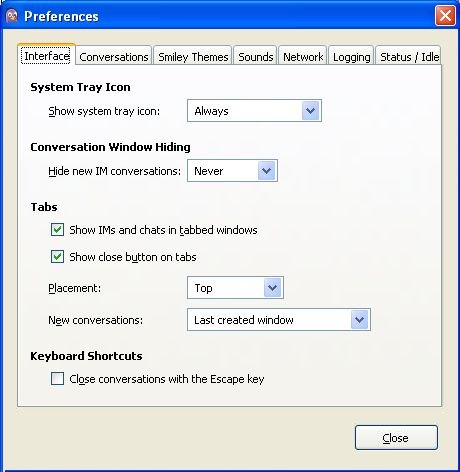
- Click the Network tab:
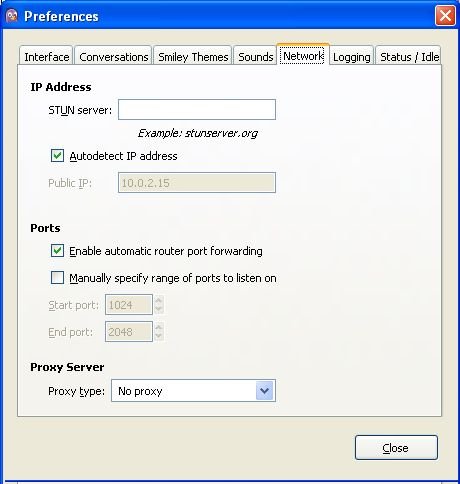
- For Proxy type, select HTTP. Additional fields appear under that option.
- Enter the Host address and port number of your HTTP proxy.
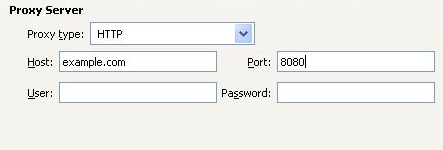
- Click Close.
When you're done with the proxy
When you are done using a proxy, particularly on a shared computer, return the settings you've changed to their previous values. Otherwise, those applications will continue to try to use the proxy. This could be a problem if you don't want people to know that you were using the proxy or if you were using a local proxy provided by a particular circumvention application that isn't running all the time.





